Overlords: Addendum 5. Case Studies in Technocratic Custodianship
Institutional priests of the post-dynastic order

Part 11 of the Overlords series established the central diagnostic frame: technocratic custodianship as the successor regime to dynastic schema control. Where Part 10 dissected the ruling stratum—those securing continuity through bloodline, land, and theological theatre—Part 11 tracks the shift: from aristocratic inheritance to algorithmic legitimacy.

This Addendum extends that analysis through case studies illustrating how procedural custodians—auditors, certifiers, standards bodies, ESG gatekeepers—now act as post-dynastic heirs. These institutions don’t merely enforce norms; they define recognition itself. They determine what counts as legal deployment, ethical AI, sustainable investment, or responsible development—not through fiat, but through compliance frameworks ritualised into legitimacy.
Context is drawn from previous Overlords mappings:
- Coders and Protocol Engineers (Part 7 & Addendum 1) inscribe logic; custodians decide which inscriptions are permitted.
- Operators (Part 8 & Addendum 2) wield control through interfaces; custodians control the interfaces themselves.
- Oligarchs (Part 9 & Addendum 3) package power through capital; custodians package it through scoring systems.
- Rulers (Part 10 & Addendums 4a/4b) inherit through lineages; custodians inherit via procedural permanence.
In this schema, technocratic entities do not merely execute power—they define its boundaries, set its conditions, and secure its reproduction. Audit becomes consecration. Metrics become ritual. Recognition becomes sovereignty.
Case Study 1: BlackRock / ESG — Recognition Circuits
Origin Mechanism — sustainability reframed as fiduciary test
When Larry Fink wrote to global CEOs in 2018, telling them that companies without a “social purpose” risked losing BlackRock’s support, it was not rhetorical flourish—it was a signal that the world’s largest asset manager was re-coding legitimacy. Climate risk, labour practices, and supply chain ethics were no longer voluntary disclosures for reputational management. They became fiduciary criteria. ESG scores, produced by vendors like MSCI and Sustainalytics, became the new recognition filters.
But the authorship of this regime did not sit in BlackRock alone. Frameworks emerged upstream—UNPRI (2006), WEF white papers, BIS system-risk memos—all framing sustainability as financial duty. Ratings firms translated these into proprietary models, each weighting factors differently, each protected by opacity. The claim was neutrality, the function coercion. If you wanted access to the largest capital pools—passive funds, sovereign wealth vehicles, global index trackers—you had to play by these scoring rules. No law was passed. No parliament voted. Yet access to capital was rewritten as a test you could only pass by clearing private thresholds.
Integration Pathway — indices as invisible regulators
The real enforcement channel was financial plumbing. ESG criteria slipped into index methodologies at FTSE Russell, S&P Dow Jones, and MSCI. Stewardship codes—revised in the UK in 2020—set formal expectations for institutional investors. Pension funds and sovereign wealth funds like Norway’s GPFG and Japan’s GPIF rewired their mandates around ESG screens. Development banks, including the IFC and EBRD, embedded ESG benchmarks into their lending toolkits.
Most decisive was the rise of passive capital. By the early 2020s, index-tracking funds controlled over 40% of U.S. equity fund assets. Once ESG screens were in the index, capital automatically flowed through them. Firms were not being regulated by governments. They were being governed by allocation logic.
Functional Role — capital replaces law as discipline
By 2020, global sustainable investment had reached US$35.3 trillion . That capital was not neutral—it was channelled by ESG scores. Ratings from Refinitiv, Moody’s ESG Solutions, and S&P Global determined who was deemed investable.
Entire countries felt the effect. In Brazil, deforestation risk in the Amazon did not trigger formal sanctions—but it did trigger spread penalties and index-eligibility pressures. Sovereign debt became more expensive. Policy shifted, not because voters or legislators forced it, but because the cost of borrowing climbed. ESG functioned as discipline without diplomacy. Law was bypassed. Recognition came through pricing.
Methods of Maintenance — compliance as treadmill
Once inside the ESG system, firms cannot step off. Disclosures are continuous: quarterly filings aligned with TCFD or the new ISSB standards. Ratings surveillance is constant: controversy screens, governance downgrades, and factor re-weightings that shift the target. MSCI, for example, reserves override powers that can reclassify a company overnight.
This is not a one-time hurdle. It is a treadmill. The taxonomy itself evolves: the EU’s Platform on Sustainable Finance revises definitions; weightings change; factor logic is updated. For firms dependent on external finance, opting out is impossible. Compliance becomes perpetual motion.
Visibility Gradient — optics in the open, thresholds in the dark
The surface layer is carefully staged. Fink’s letters, glossy ESG dashboards, annual stewardship reports—all public, polished, performative. But the decisive mechanics sit in shadow. Index committees decide inclusion and exclusion. Ratings vendors hold proprietary weightings and override protocols.
FTSE Russell’s exclusion lists are public; the logic behind inclusion is not. S&P Global publishes high-level scoring rubrics; the thresholds that tip a company from “compliant” to “excluded” remain paywalled or NDA-sealed. Recognition is public in symbol, private in substance.
Durability Horizon — allocation plumbing outlasts politics
By 2023, ESG had hardened into the plumbing of global finance. Procurement rules referenced ESG benchmarks. Credit models priced loans by ESG risk. Insurance covenants required disclosure. Even if cabinets shifted—say, in Australia or Brazil—the market still priced firms and states through ESG filters.
Once embedded in benchmarks and contracts, ESG became self-perpetuating infrastructure. Standards could change—S&P rebalanced its environmental weightings in 2022—but the custodial logic remained. CEOs retire, governments rotate, but the scoring system endures. Recognition becomes a permanent audit, a circuit of legitimacy that no ballot can override.
Proponents insist ESG internalises long-term risks—climate exposure, labour conditions, governance stability—into financial decision-making. That rationale is not fabricated. But the effect is structural coercion: what was framed as risk awareness became a filter of eligibility, enforced not by law, but by metrics.
Case Study 2: BIS / CBDC Pilots — Programmable Money as Protocol Control
Origin Mechanism — inclusion rhetoric, control design
The BIS Innovation Hub (2019) justified central bank digital currencies (CBDCs) with inclusion, efficiency, and anti-fraud rhetoric. These were partial truths. The deeper purpose was programmable enforcement. Agustín Carstens, BIS General Manager, put it bluntly in 2020: with CBDCs, central banks will have “absolute control” over the rules of use and “the technology to enforce that.”
Projects like mBridge (China, UAE, Hong Kong, Thailand) and Dunbar (Australia, Singapore, South Africa) piloted CBDCs where rules are encoded in the unit of exchange. Payment execution is conditional: who pays, how much, for what, and under which jurisdiction. No court, no ex-post remedy—the ledger enforces compliance at the moment of transaction.
U.S. resistance was explicit. By 2023, Florida, Texas, South Dakota passed pre-emptive CBDC bans. Rep. Tom Emmer tabled the CBDC Anti-Surveillance State Act. Formal issuance was blocked—but the architecture migrated into private hands.
Integration Pathway — from pilots to Zero Trust rails
Programmable money logic persists in stablecoins and instant-payment rails.
- USDC (Circle, 2018) can freeze wallets, blacklist addresses, enforce rules in smart contracts
- PYUSD (PayPal, 2023) and Paxos tokens follow the same model
- FedNow (July 2023) provides programmable instant settlement without calling itself a “digital dollar.”
The integration is not just financial. It is architectural. The model is Zero Trust: no transaction is assumed legitimate, no wallet permanently authorised. Each payment requires renewed proof of identity and eligibility. KYC becomes continuous, not one-off. Eligibility depends on live authentication against compliance databases, sanctions lists, and risk scores.
This is the opposite of cash. Cash confers legitimacy at handover. CBDC/stablecoin rails make legitimacy contingent on continuous re-verification: prove who you are, where you are, and why you are paying—every time.
Functional Role — permissioning at the transaction layer
Programmable money shifts regulation into the unit itself:
- Identity binding: every wallet tied to digital ID, biometrics, or device profile
- Purpose coding: spend limited to pre-approved categories (food vouchers, stimulus)
- Geofencing: payments restricted by location
- Eligibility proof: KYC tiers define ceilings and access.
Concrete examples already exist. In 2022, Circle froze USDC tied to OFAC-sanctioned wallets with no judicial process. ECB’s digital euro prototypes include wallet-level limits linked to ID tiers. BIS’s Project Sela trialled transaction ceilings enforced by KYC depth.
Bitcoin is folded into this regime. Its transparent ledger enables total traceability. Chainalysis, TRM Labs track wallet behaviour for regulators. OFAC blacklists addresses, and exchanges freeze flagged coins. Visibility—once sold as trust—becomes compliance.
Methods of Maintenance — version churn and surveillance feeds
The system runs on continuous update:
- Sanctions list ingestion
- Smart contract revisions
- Wallet rules, API changes.
Zero Trust logic ensures no clearance is permanent. Identity must be reproven, eligibility re-checked, on every transaction. Vendors like Circle or Fireblocks push backend policy updates invisibly. BIS and FATF committees circulate new AML/KYC modules.
Surveillance analytics sustain the loop. Wallet activity, IP data, device fingerprints, behavioural flags—all scored in real time. The system is not simply payments—it is continuous background investigation.
Malevolent Usage — tested in the open
The benign case is inclusion, speed, fraud prevention. The coercive use is already evident:
- Canadian trucker protests (2022): accounts and wallets frozen for political dissent
- Activist projects like Panquake: denied banking services, now fighting in an Icelandic court
- Negative rates / expiring money: Chinese pilots tested stimulus funds that vanish if unspent
- Automated penalties: fines, taxes, or court orders deducted directly without contest
- Intelligence integration: programmable rails offer agencies direct visibility, mapping social and political networks through spend.
Privacy technologies are targeted. Samourai Wallet developers (arrested April 2024) and Tornado Cash developers (sanctioned Aug 2022) were prosecuted not for fraud but for enabling untraceable spend. Monero has been delisted by exchanges. Resistance is not illegalised—it is structurally excluded.
Visibility Gradient — inclusion optics, hidden overrides
The optics are benign: BIS panels, IMF reports on inclusion, ECB wallet demos. Stablecoin issuers publish dashboards and attestations.
The controls are opaque: override keys, kill-switches, vendor NDAs. USDC blacklists without appeal. ECB committees discuss programmable features behind closed doors. Privacy “tiers” are offered—but only as permissioned concessions, not rights.
Durability Horizon — rails beyond repeal
CBDCs may be banned in some jurisdictions, but the rails persist. Visa and Mastercard settle stablecoins. PayPal mints its own. FedNow embeds programmable settlement in domestic payments. Once banks and merchants integrate, reversal is prohibitively costly.
Digital identity closes the loop. Wallets are inseparable from ID schemes: ISO/IEC 18013-5 mobile licences, World Bank ID4D, WEF Known Traveller. Payment becomes indistinguishable from identity proof.
Issuers may rotate—central bank, fintech, consortium. The permissioning remains. Money is no longer a neutral token—it is a live, revocable credential.
Case Study 3: Standards and Certification Mesh — OECD, ISO/IEEE, BSI/TÜV, NIST, and Municipal Audits
Origin Mechanism — fairness and safety recoded into protocols
What dynasties once legitimated through ritual, and legislatures through statute, standards bodies now legitimate through clauses. OECD AI Principles (May 2019) framed “fairness, transparency, accountability” as global norms. ISO and IEEE transformed those principles into technical controls: ISO/IEC 42001 for AI management systems, IEEE 7000-series for ethical alignment. National agencies like NIST published risk frameworks; legacy certifiers like BSI and TÜV adapted their industrial seals to digital systems.
Cities imported the same logic. New York City’s Local Law 144 (2021) required bias audits for automated hiring. Legitimacy no longer derived from democratic deliberation about what counts as fair; it was conferred by passing a statistical test suite blessed by an accredited auditor. Ethics became machine-readable. Recognition meant a mark.
Integration Pathway — standards by reference, certification by mandate
The pathway is indirect but binding. Governments incorporate standards by reference—the EU cites ISO norms in harmonised lists; U.S. agencies adopt NIST baselines for procurement. OECD categories seed the taxonomy, ISO/IEEE publish the testable clauses, and notified bodies enforce them.
Certification firms operationalise the mesh. A cybersecurity vendor needs a BSI Kitemark. A turbine needs a TÜV seal. A hiring platform needs a bias-audit certificate to sell in New York. Procurement contracts, liability insurance, and platform onboarding all hinge on possession of these marks. Legislatures gesture at “safety” or “fairness.” The decisive test lives elsewhere.
Functional Role — seals as market passports
The role is permissioning. Certificates and audit attestations act as passports for market entry. They decide who may sell, ship, or integrate.
The codifiers write the rulebook; the certifiers keep score. OECD and ISO translate principles into controls; BSI, TÜV, NIST, and municipal auditors apply them. Together, they define the gate. A system without the seal is excluded—not because a law bans it, but because no buyer, insurer, or regulator will touch it. Regulation dissolves into law-by-reference.
Methods of Maintenance — perpetual updates under opaque thresholds
This regime is self-renewing. ISO revises standards on a five-year cycle. IEEE working groups ballot revisions. NIST updates risk frameworks annually. Cities update bias-audit rubrics. Certification bodies conduct surveillance audits, renewals, and continuous monitoring.
Thresholds remain sealed. Test suites sit behind paywalls. Negative-vote rationales in ISO committees are not public. Override committees at certifiers can downgrade or suspend marks without external review. Vendors face a treadmill of documentation, model cards, risk files, and audits. The target shifts. The loop never ends.
Visibility Gradient — logos public, rulebooks hidden
The optics are visible: OECD white papers, ISO logos, TÜV seals, bias-audit certificates. These badges perform transparency.
The decisive criteria are hidden:
- The mapping of OECD principle → ISO clause → conformity test
- The weightings of bias-audit rubrics
- The composition of ISO and IEEE committees
- The override mechanisms inside BSI and TÜV.
To outsiders, the regime appears as a set of public badges. But the gates are controlled by committees operating in private, under paywall, or behind NDAs.
Durability Horizon — supply-chain embedding outlives politics
Once embedded in procurement, liability, and insurance, standards and certification outlast cabinets and mayors. A government can repeal a rule, but the supply chain still demands a TÜV seal, an ISO mark, or a bias-audit certificate.
Codification and certification form a custodial architecture. Standards update; seals renew; committees rotate. The regime persists because contracts, insurers, and platforms will not transact without it. Governance is infrastructural. Custodianship remains.
Advocates argue standards and audits guarantee safety, interoperability, and fairness in complex systems. This is not untrue. But the same mechanisms become coercive when access to markets, finance, and liability hinges on clearing opaque tests set by committees beyond democratic reach.
Case Study 4: EU AI Act — Algorithmic Trusteeship
Origin Mechanism — safety reframed as eligibility
The EU AI Act, proposed in April 2021 and passed by the European Parliament in March 2024, presents itself as the world’s first comprehensive AI law. Its rhetorical anchor is safety. Not liberty, not innovation, not public deliberation—safety. Legitimacy is recoded: the question is no longer whether a system ought to exist, but whether it satisfies a taxonomy of controls authored upstream.
The Act stratifies AI into four risk tiers: unacceptable (banned), high-risk (regulated), limited (labelled), and minimal (unconstrained). This taxonomy is not descriptive, it is allocative. Placement determines viability. Passage from forbidden to permissible is not negotiated in public, but earned by clearing documentation and audit.
This is not censorship in the old sense—it is trusteeship. Developers do not argue their case in open court. They must demonstrate conformity with predefined controls. Recognition flows not from outcome but from process. Legitimacy becomes a function of checklist clearance, structured by committees no voter can access.
Integration Pathway — delegation by design
The Act does not regulate directly. It delegates. The European Commission sets the frame but passes responsibility into a procedural relay:
- Notified bodies, designated by member states, conduct conformity assessments
- Providers must maintain technical files: dataset provenance, risk management logs, governance documents
- Post-market monitoring compels ongoing surveillance: incident reporting, performance tracking, and periodic updates.
This is staged governance. Pre-deployment audits are followed by CE-style declarations, then continuous monitoring after release. But the benchmarks are not written in the Act. They are embedded in harmonised standards published by ISO, CEN/CENELEC, and IEEE. These standards—referenced, but not reproduced—become the real law. Parliament gestures; the standard decides.
Functional Role — permissioning displaces contestation
The Act does not regulate outputs; it regulates eligibility. Certain systems—such as real-time biometric surveillance in public—are banned outright. Others, deemed “high-risk,” require certification before deployment.
The effect is inversion. Political contestation—whether a system should exist—is displaced by technical compliance. The gate is not parliamentary vote but file inspection: does the system document its training data? does it log its decisions? does it conform to ISO 42001 or CEN JTC-21?
Procurement officers, insurers, and financiers reinforce the gate. A system without a conformity mark cannot be underwritten, purchased, or deployed. The Act does not need to enforce with sanctions. Exclusion happens by default refusal. Non-compliance is not illegal—it is ineligible. Law becomes architecture.
Methods of Maintenance — shifting standards, opaque committees
Compliance is perpetual. Providers must maintain:
- Dataset and model documentation (provenance, versioning)
- Audit trails for decisions and outputs
- Monitoring for incidents post-deployment.
But the decisive criteria are not in the statute. They are in referenced standards authored by ISO/IEC JTC 1/SC 42, IEEE 7000 committees, CEN working groups. These documents are paywalled, balloted, and managed by technocratic committees. What counts as bias, explainability, or robustness shifts over time—but always outside public scrutiny.
Opacity is structural. Parliament issues the law; notified bodies apply the harmonised standards; standards are written by overlapping committees of vendors, consultants, and state-aligned technocrats. To the public, the Act appears as transparent regulation. In practice, it is a conduit into procedural codes that move beyond reach.
Visibility Gradient — law public, test hidden
The AI Act itself is visible: press releases, legal texts, high-level principles. Its categories—safety, accountability, transparency—are widely cited.
But the operational test is buried. The conformity modules, the harmonised standards, the criteria used by notified bodies—these sit behind paywalls, NDAs, and committee structures. Even regulators often defer to certification authorities, who themselves depend on standards written by private committees.
Visibility is symbolic. The real gatekeeping is procedural, hidden in annexes, cross-walks, and technical thresholds invisible to the end user.
Durability Horizon — permanent procedural dependency
Once embedded in procurement rules, liability templates, and platform onboarding, the AI Act’s permissioning logic becomes irreversible. Even if a future Commission loosens restrictions, the referenced standards persist. Committee inertia and vendor lobbying ensure the gate remains.
A vendor’s eligibility to sell across Europe depends not on advocacy but on auditability. A public-sector AI deployment depends not on legislative approval but on whether it clears a conformity check. Each revision of ISO, IEEE, or CEN standards quietly updates the gate without any parliamentary vote.
The authority here is not in permanence of statute but in permanence of dependency. Governments rotate. Commissioners retire. But the compliance mark remains the cost of participation. Once installed, the gate is the game.
Advocates insist the Act guarantees baseline safety, harmonises the single market, and protects citizens against harmful AI. Those claims are real. But the structure converts safety into eligibility, enforced through standards by reference. Contestation dissolves; the gate persists.
Case Study 5: Sovereign Wealth Funds — Hybrid Heirs
Origin Mechanism — stewardship replaces sovereignty
Sovereign Wealth Funds (SWFs) did not arise from dynastic right or democratic mandate. They emerged as fiduciary substitutes—technocratic containers for surplus revenues, designed to mute politics and defer consumption.
Norway’s Government Pension Fund Global (GPFG) was legislated in 1990, operational in 1996, as a firewall between oil revenues and political interference. Its legitimacy was pinned to fiscal rules and custody by the central bank. Temasek Holdings, established in 1974 in Singapore, consolidated state-owned enterprise assets into a holding-company structure while adopting the posture of a private corporation. Saudi Arabia’s Public Investment Fund (PIF) was founded in 1971, but only reactivated at scale under Vision 2030 after 2015, repositioned as a geopolitical lever under technocratic guise.
Across these cases, legitimacy is reframed. There is no voter accountability, no royal claim. Instead, capital is presented as intergenerational equity, managed by professional boards, benchmarked against indices, and overlaid with ESG rhetoric. Sovereign ownership is recoded as neutral stewardship—rule-bound, depersonalised, and performance-indexed.
Integration Pathway — indices and codes as filters
Allocation practices are channelled through global indices (MSCI, FTSE, S&P), stewardship codes (UN PRI, ICGN, UK Stewardship Code), and third-party ESG frameworks (SASB, TCFD, ISSB).
- Norway’s GPFG enforces an exclusion list based on ethical guidelines drafted by its Ministry of Finance and executed by Norges Bank Investment Management (NBIM). Firms in tobacco, coal, weapons, or human rights controversies are screened out.
- Temasek structures its portfolio with geographic and sectoral balance, wrapped in annual sustainability reporting aligned to the Task Force on Climate-Related Financial Disclosures (TCFD).
- Saudi PIF integrates ESG language indirectly—via co-investments and partnerships with ESG-compliant funds—offshoring legitimacy through alliances.
In each case, compliance with external taxonomies becomes the interface with global capital markets. The funds export norms by allocating capital according to rules authored elsewhere.
Functional Role — capital as gatekeeper
These funds act as structural gatekeepers. Their decisions define which firms, projects, or countries can access capital. ESG overlays serve as strategic levers.
- GPFG’s Council on Ethics operates as a quasi-sanctions regime, excluding firms without legislation or diplomacy.
- Temasek imposes climate-alignment metrics on its portfolio companies, transmitting Singapore’s governance style into multinational boardrooms.
- PIF directs capital to condition domestic reform and foreign compliance, particularly in infrastructure projects across Africa and Southeast Asia.
Counterparties must internalise compliance architectures—reporting formats, engagement protocols, risk models—simply to receive funding. Norms are exported through allocation strings. Legitimacy is priced into the deal.
Methods of Maintenance — mandates and opacity
Continuity is secured through formal mandates, rotating stewardship codes, and asset-manager guidelines.
- GPFG’s investment policy is periodically updated by the Ministry of Finance but operationalised independently.
- Temasek functions as a corporate board, with Singaporean ministers as ultimate custodians.
- PIF is chaired by Mohammed bin Salman, its governance wired into Vision 2030 subcommittees.
Allocation is routed through offshore vehicles (SPVs in Luxembourg, Cayman, Jersey), opaque investment committees, and NDA-bound co-investments. Oversight mechanisms exist but the decisive thresholds—what is excluded, who is funded, which risks are tolerated—remain gated. Transparency is summarised, not disclosed.
Visibility Gradient — dashboards outside, committees inside
The public optics are polished:
- GPFG publishes holdings lists, voting records, and annual reports.
- Temasek releases glossy sustainability frameworks and impact dashboards.
- PIF showcases global investments and flagship projects.
The decisive infrastructure remains obscured: exclusion models, ESG scoring thresholds, internal deliberations. GPFG’s ethical screens are public in principle but implemented via external index providers. Temasek describes its climate tools only in broad strokes. PIF’s allocations are presented as strategy but function as geopolitical bargaining. The public sees brands and metrics. Recognition is conferred behind closed committees.
Durability Horizon — custodial capital outlasts rulers
Once wired into benchmarks, co-investment consortia, and insurance templates, the allocation logic of SWFs is self-reinforcing.
- GPFG cannot re-enter tobacco or coal without undermining its global legitimacy.
- Temasek cannot abandon climate alignment without collapsing its investor alliances.
- PIF’s geopolitical allocations will persist beyond MBS if infrastructure and regional integration are already financed.
Technocratic legitimacy becomes custodial. Cabinets rotate. Boards shift. Princes rise and fall. The screens persist.
SWFs do not simply invest capital. They define the conditions under which capital itself can move.
Defenders stress that sovereign funds stabilise economies, save for future generations, and professionalise state finance. Those claims are valid. Yet once norms are embedded in allocation screens, sovereign funds operate as unaccountable regulators of capital flows, exporting governance conditions through the promise—or denial—of investment.
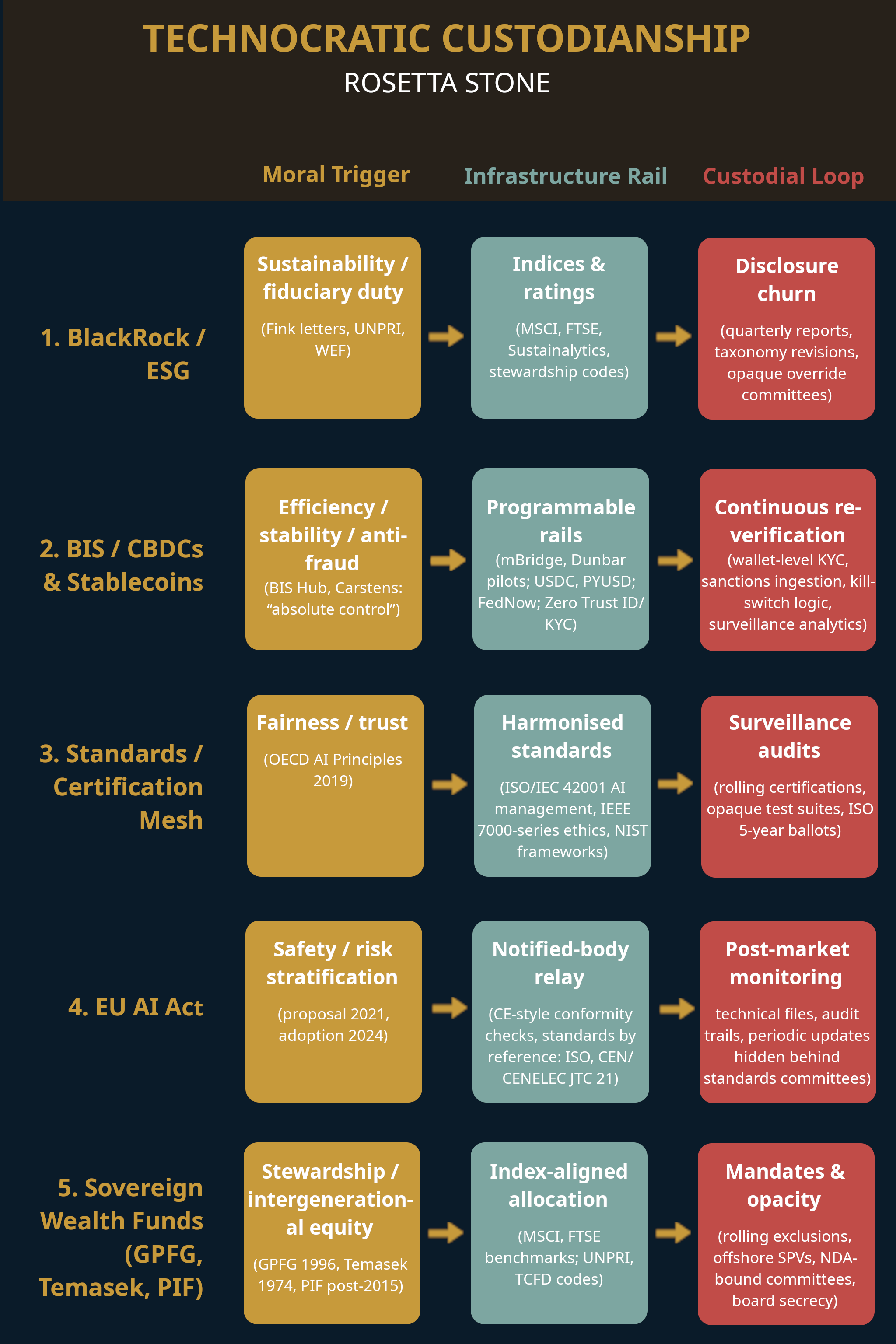
Synthesis: Patterns Across Custodial Regimes
Origin Mechanism — safety, sustainability, stewardship as substitutes for sovereignty
The old anchors—lineage, mandate, election—are displaced.
- BlackRock / ESG: fiduciary duty reframed as climate and social scoring (Larry Fink’s CEO letters, 2018 onward).
- BIS / CBDC: financial stability reframed as programmable compliance (BIS Innovation Hub, 2019; Carstens, 2020: “absolute control”).
- Standards / Certification Mesh: fairness and trust recoded into management clauses (OECD AI Principles 2019; ISO/IEC 42001 AI management; IEEE 7000-series ethical standards).
- EU AI Act: “safety” operationalised as risk taxonomy (proposal 2021, adoption 2024, with banned/high/low-risk strata).
- SWFs: intergenerational equity recoded as technocratic stewardship (Norway GPFG 1996; Temasek 1974; Saudi PIF reactivated 2015).
Across these regimes, legitimacy is transferred from political contestation to procedural neutrality. “Sustainability,” “safety,” and “stewardship” function as moralised triggers for procedural clearance. Recognition is not won from citizens—it is granted by clearing structured thresholds.
Integration Pathway — standards, indices, rails, mandates, zero-trust checks
The conduits bypass parliaments.
- ESG: index rules (MSCI, FTSE Russell), stewardship codes (FRC 2020), sovereign mandates (GPIF, GPFG).
- CBDCs / stablecoins: BIS pilots (mBridge, Dunbar), private rails (USDC 2018, PYUSD 2023), FedNow (2023). Zero-trust architecture means every transfer requires re-verification of ID, wallet, and purpose.
- Standards mesh: OECD ethics → ISO/IEC & IEEE clauses → certification firms (BSI, TÜV, NIST) → procurement.
- EU AI Act: statutory frame delegates to harmonised standards enforced by notified bodies.
- SWFs: allocation rules tethered to global benchmarks, ESG frameworks, and stewardship codes.
Integration operates through reference and procurement. Standards are cited in laws; indices hardwired into mandates; compliance marks required in tenders. In zero-trust finance, eligibility is not permanent—it must be continuously reproven, embedding governance in infrastructural rails rather than statutes.
Functional Role — permissioning replaces politics
The function converges: custodians decide who may participate.
- ESG: scores gate capital flows.
- CBDC/stablecoins: wallets and rails gate every transaction at the protocol layer, demanding continuous identity proofs.
- Standards/certification: seals determine market entry.
- EU AI Act: conformity marks condition system deployment.
- SWFs: exclusion lists and screening criteria govern who receives sovereign capital.
Politics does not vanish—it is displaced. Contestation is sidestepped. What fails eligibility is not outlawed, only rendered ineligible. Permissioning is regulation encoded as infrastructure.
Methods of Maintenance — audits, loops, re-verification, opacity
All cases depend on perpetual compliance cycles.
- ESG: quarterly disclosures, taxonomy churn, vendor override committees.
- CBDCs / stablecoins: sanctions list ingestion, wallet-rule updates, real-time KYC checks under zero-trust logic.
- Standards / certifiers: ISO/IEC five-year revisions, rolling audits, opaque ballots.
- EU AI Act: technical files, conformity renewals, post-market monitoring.
- SWFs: mandate revisions, NDA-bound co-investments, offshore SPVs.
The loops are opaque. The decisive thresholds—ratings weights, protocol overrides, identity scoring engines—reside inside vendor logic or committee procedures. Compliance shifts, but always under technocratic custody.
Visibility Gradient — brands perform, gates conceal
Public optics are polished:
- Larry Fink letters and ESG dashboards.
- BIS conference demos and CBDC wallet prototypes.
- OECD principles and ISO logos.
- EU AI Act press releases.
- SWF annual reports and sustainability dashboards.
But decisive gates remain sealed: model weights, kill-switches, override keys, committee ballots, KYC scoring thresholds. Logos are visible; recognition is conferred in the dark.
Durability Horizon — infrastructure outlives rulers
Custodial architectures persist beyond governments or boards.
- ESG: filters embedded in indices and mandates.
- CBDCs / stablecoins: programmable rails and zero-trust identity binding continue regardless of political bans.
- Standards mesh: recertification cycles and harmonised clauses persist indefinitely.
- EU AI Act: compliance marks bind procurement even if statutes soften.
- SWFs: allocation screens embed norms in global capital flows.
Governments rotate, CEOs retire, princes fall. But once coded into benchmarks, rails, contracts, and ID-linked wallets, reversal is structurally prohibitive.
Pattern
Across domains, technocratic custodianship converts moralised principles into procedural filters. Recognition is no longer sovereign command or public assent—it is infrastructural eligibility. ESG scores, CBDC wallet checks, conformity marks, and SWF exclusions are the new sovereign signs. Compliance loops plus zero-trust verification ensure recognition is never permanent, only continuously re-earned.
Closing Frame — The Fracture Point
Technocratic custodianship completes the schema. Where dynasties consecrated through ritual, and republics through law, technocrats consecrate through metrics. The sovereign seal has been replaced by the auditor’s stamp.
This is the post-dynastic apex. Authority no longer flows from lineage or from vote, but from passing perpetual audits. Recognition is conferred through compliance loops: ESG scores, CBDC rails, ISO clauses, AI conformity marks, SWF screens. The gate does not open by command or consent, only by clearance.
The fracture lies here: governance no longer requires visible rulers. Custodianship persists even if custodians vanish. Standards update, indices rebalance, rails version, funds rotate—but the recognition infrastructure remains.
Power without face. Legitimacy without end. What once was law or crown is now protocol. The gate is the game.
Published via Journeys by the Styx.
Overlords: Mapping the operators of reality and rule.
—
Author’s Note
Produced using the Geopolitika analysis system—an integrated framework for structural interrogation, elite systems mapping, and narrative deconstruction.



