The Operators: Part 1. Neocons
An operator’s-eye diagnosis of “neoconservatism”: a crisis-dependent module that sustains U.S. primacy via placements and process control—judged by actions and outcomes, not slogans.

Overlords Part 8 defined the Operating Class as a permanent managerial layer—neither hereditary elites nor elected officials—tasked with keeping the runtime intact. Applying that lens here, we weigh what the neocon cohort did and produced over what it said. The actions are observable: placement into planning and policy billets; drafting guidance that becomes default; shaping intelligence, legal rationales, sanctions, and arms flows; conditioning allies; saturating media frames; expanding authorities and budgets; and re-entering after scandal through think-tank and board refuges. The outcomes are likewise traceable: normalisation of pre-emption after 2001; expeditionary wars and regime-change campaigns; hardened alliance commitments and NATO expansion; durable surveillance and detention architectures; crisis-time consensus in major outlets; and the recurring reappointment of the same personnel across administrations.

Against that baseline sit the stated motivations and goals: deterrence and alliance credibility, democratic peace and human rights, prevention of catastrophic risks, stewardship of a rules-based order. We register those aims as sincere for many actors. The diagnostic claim is narrower: in practice, the system selects and retains methods that turn these aims into operational defaults that keep American primacy non-negotiable, especially under crisis. Self-presentation—humanitarian and legal language, multilateral veneers, prizes and fellowships—performs appearance laundering, translating placement into public legitimacy and narrowing the range of “serious” options to calibrated versions of enforcement.
On this reading, “neoconservatism” names a security-operator module rather than an ideological school. The test is empirical: actions and outcomes vs. stated motivations and goals. The companion Addendum 1. Neocon Case Studies follows fourteen figures by placements taken, levers pulled, and results obtained, so the assessment rests on what was done and what it yielded—not on declarations of why.
What is a Neocon? Branding vs Function
By their own account, neoconservatives aim to deter aggression, reassure allies, advance democratic norms, and prevent catastrophic threats through forward-leaning policy. Those stated motivations matter; many actors likely hold them sincerely. The diagnostic question here is what their actions and outcomes show. Across decades, the observable pattern is placement into policy nodes (Pentagon, State, NSC, congressional committees), production of guidance that becomes default, orchestration of sanctions and arms flows, and sustained presence in major outlets where the range of options narrows toward coercive measures. The outcomes are consistent: normalisation of pre-emption after 2001, expeditionary wars and regime-change attempts, expansion and hardening of alliance commitments, growth in security authorities and budgets, and recurrent reappointment of the same personnel after setbacks.
The label “neoconservative” functions as a rallying frame for heterogeneous biographies—ex-liberals and Cold War Democrats alongside hawkish Republicans—while the operational constant sits beneath: American primacy kept non-negotiable. Jeane Kirkpatrick’s tolerance for authoritarian partners, John Bolton’s coercive unilateralism, and Robert Kagan’s liberal-order rhetoric differ in register but converge in effect when installed as policy: enforcement takes precedence over restraint. The coherence comes less from a shared doctrine than from a shared placement cycle—government ⇄ think tanks ⇄ media ⇄ boards—that converts aims into defaults during crises.
Self-presentation does additional work. Humanitarian and legal language, multilateral veneers, prizes, fellowships, and editorial platforms provide appearance laundering that translates institutional placement into public legitimacy. This does not prove insincerity; it shows how the system selects and retains actors whose methods align with crisis management and primacy maintenance. On that reading, “neoconservatism” is best treated as a security-operator module rather than an ideological school: judge it by the record of actions and outcomes, and the persistence of those outcomes across cycles, not by the stated goals that accompany them.
Brand language—democracy, moral clarity—also fuses with Israel-security framing. In practice, the “ally reassurance” register serves as a conveyor, moving U.S. force and sanctions toward Israel’s adversaries by default.
Origins – Intellectual Seedbed
The first-wave neocon writers set out to restore strategic clarity after Vietnam and détente, defend an embattled liberal order, and deter adversaries while supporting allies—Israel’s post-1967/1973 vulnerability included. The actions that followed were editorial and institutional: building journals (The Public Interest, Commentary), convening conferences, and seeding fellowships that identified and socialised talent. The outcomes are visible in placement, not readership metrics: publication credits became reliable signals for recruitment into policy schools, Pentagon and State staff jobs, and think-tank roles. What began as argument quickly doubled as a credential-signaling pipeline that moved apprentices—Wolfowitz, Perle, Abrams—toward enforcement posts.
Jeane Kirkpatrick’s “Dictatorships and Double Standards” offered the clearest statement of purpose: prioritise stability against totalitarian expansion, manage democratic transitions prudently, and avoid moral grandstanding that topples anti-communist allies. In practice, the essay functioned as operational shorthand. The outcome pattern—selective tolerance for authoritarian partners deemed strategically useful, heightened pressure on left-aligned regimes, and supportive cover for covert and proxy activity in Central America, parts of Africa, and Asia—shows doctrine translating into rules of engagement.
Many early figures were former liberals or socialists. Their conversion stories furnished a moral authority narrative—hard lessons learned, utopianism shed—which played well in the post-Vietnam milieu. The measurable effect, however, was circulation: journals → fellowships → staff billets → advisory boards → back to publishing platforms. Self-presentation emphasised ideals (democratic peace, human rights, deterrence); the system converted those ideals into placement advantages. The same articles that argued for clarity also laundered appearance—marking authors as serious, prudent, and therefore promotable—narrowing the field of “responsible” candidates to those already aligned with the enforcement runtime. Commentary / WINEP-adjacent circuits doubled as an Israel-policy pipeline: publishing conferred not only U.S. credibility but Israel-security access, accelerating fellowships and billets for operators aligned with that frame.
Read this way, the seedbed wasn’t an autonomous realm where ideas decided policy; it was an imprinting stage where ideas doubled as filters. Measured by actions and outcomes, the magazines and manifestos did less to persuade the mass public than to staff the machine. The intellectual origins produced fewer philosophers than operators-in-training, with sincerity of motive compatible with, and often selected by, a system that rewards crisis-ready custodians of primacy.
Operators in Practice – Bureaucratic Enforcers
The seedbed supplied language; the operators translated it into defaults. Their stated aims—prevent peer rivals, deter catastrophic threats, shorten wars by decisive action—arrived as guidance documents, process changes, and placement into nodes where options could be formatted. The measurable pattern is not speeches but wiring: who drafted the templates, who controlled the evidentiary flows, and how inter-agency pathways were rerouted so that enforcement read as prudence.
- Paul Wolfowitz’s record shows how doctrine becomes baseline. Framed as preserving post–Cold War stability and deterring challengers, his 1992 Defense Planning Guidance set prevention of peer competitors as a core task. After 9/11, as Deputy Secretary of Defense, he treated that template not as one option among many but as planning architecture—with pre-emption and Iraq installed as the working plan.
Outcome: the prevention logic migrated from a staff paper into the operating system of U.S. force employment. - Douglas Feith’s remit, presented as fixing analytic gaps and integrating policy with intelligence, produced a different lever: the Office of Special Plans. Its function was alternative vetting—curating and formatting raw reports to align with a regime-change threat model.
Outcome: confirmation-heavy pipelines that lowered the evidentiary bar for war decisions and raised it for restraint, shifting the burden of proof inside the bureaucracy. - Richard Perle’s advisory role illustrated the off-stage node. Cast as drawing on outside expertise to improve decision quality, the Defense Policy Board became a synchroniser of strategy discussions with industry and contractor perspectives.
Outcome: procurement priorities and coercive policy moved in tandem, with consultation structures that amplified escalation-friendly assumptions while muting cost and stabilisation risks. - Donald Rumsfeld’s modernisation push—agility, transformation, lighter footprint—created managerial cover for this ecosystem. By compressing timelines, privileging lean planning, and centralising authority, his reforms accelerated the translation of templates into orders.
Outcome: faster decision cycles for Afghanistan and Iraq, coupled with postwar planning gaps that proved hard to correct once the defaults were live. - At the apex, Dick Cheney framed his office as ensuring integrated, decisive strategy in a dangerous world. Practically, the vice-presidential staff operated as a parallel command node: task forces, classified directives, and lawyered authorities that redefined surveillance, detention, interrogation, and pre-emption as standing executive tools.
Outcome: durable legal-operational frameworks that persisted across administrations and made rollback politically and procedurally costly.
Cross-walk memos between U.S. planning and Israel strategy—most starkly in 1990s–2000s Iran / Syria concepts—functioned as doctrine bridges. Intelligence triage and external ‘alt-vetting’ laundered Israel-sourced threat claims into U.S. evidentiary streams. Taken together, these are action–outcome linkages more than ideological debates. The operators stated goals—deterrence, prevention, credibility—while their placements converted those goals into routinised enforcement. Inside the machine, war was seldom a clean yes/no choice; it was the endpoint of a process whose upstream steps had already narrowed the path.
Outcomes: The Iraq operation produced large-scale civilian harm, mass displacement, institutional collapse, and second-order militant formation. Post-9/11 legal-architecture changes (detention/interrogation/surveillance) proved sticky across administrations, raising the threshold for rollback.
Diplomatic & Political Interfaces
If the Pentagon operators wired enforcement into the machine, the interface layer carried it outward and locked it in at home. Their stated aims—protect allies, deter adversaries, uphold democratic norms, keep signals clear—explain the portfolio they seek; the record shows how those aims translated into actions and outcomes that made primacy hard to contest.
- Victoria Nuland presented her work as alliance management and support for democratic sovereignty. In practice, her rotations—State → NATO → think tank → State—placed her at choke points where recognition, assistance, and cabinet-making leverage could be used to keep governments inside the preferred policy lane. The outcome was alignment as deliverable: partners calibrated to Washington’s sanctions, arms flows, and red lines. The continuity across postings mattered as much as any speech; each redeployment reactivated the same tool set under new institutional letterhead, with appearance laundering supplied by process language—“reform,” “anti-corruption,” “Euro-Atlantic integration.”
- John Bolton framed his style as clarity and leverage—no mixed signals, no illusions. His UN ambassadorship and later National Security Advisor role prioritised coercive instruments over negotiated reciprocity. The actions were pressure campaigns and strike advocacy (notably on Iran and Venezuela), procedural blockages in multilateral forums, and public red lines that narrowed the bargaining space. The outcome was a menu weighted toward escalation, with multilateral optics preserved where useful but discarded when constraining.
- Elliott Abrams described his brief as democracy promotion and crisis management. The career arc—Reagan-era Latin America, then Middle East portfolios under George W. Bush, then Venezuela envoy under Trump—shows how scandal produced rotation rather than exit. The action pattern is redeployment to new enforcement nodes when a rupture opens; the outcome is functional continuity across decades, with pardons, fellowships, and advisory roles serving as the bridge between assignments.
- John McCain and Lindsey Graham cast themselves as guardians of American leadership and the rules-based order. Their committee posts, floor speeches, and bipartisan coalitions translated into appropriations, authorisations, and alliance expansions that insulated expeditionary policy from electoral swings. The outcome was legislative ballast: budgets and mandates that outlived administrations, with patriotic framing providing the legitimacy wash that made opposition look unserious or unsafe.
On the Hill, QME statutes and missile-defense add-ons made “support for Israel” a procedural engine for broader expeditionary and sanctions budgets. Embassy moves, normalisation pushes, and Iran votes cemented the interface.
Taken together, the interface layer did what operators are selected to do: convert intentions—deterrence, reassurance, democratic solidarity—into compliance architectures abroad and appropriations certainty at home. The visible diplomacy and Senate pageantry supplied appearance laundering (process, principle, bipartisanship) while the measurable effects—aligned cabinets, synchronised sanctions and arms packages, locked-in budgets—kept enforcement running as the default.
Outcomes: Sanctions and coercive diplomacy correlated with humanitarian deterioration and governance stress in targeted states; congressional ballast translated into multi-year appropriations that sustained conflict exposure beyond initial authorisations.
Israel/Zionist Linkages — The Security Interface
Beyond U.S. primacy for its own sake, a standing U.S.–Israel security interface binds neocon operators to a second, tightly coupled runtime: Israel’s regional freedom of action and threat management. The linkage isn’t ethnic or theological; it’s institutional: donors, think tanks, lobby ecosystems, intel / military pipelines, and media nodes that convert “Israel’s security” into default U.S. enforcement scripts.
Mechanics (placement → leverage → outcome):
- Donor & foundation pipes. A stable set of diaspora and aligned philanthropies routes funding into operator platforms (fellowships, chairs, media ventures), underwriting careers between government tours. (Function: insulation.)
- Think-tank lattice. WINEP, FDD, JINSA, AEI (and their fellow networks) produce rapid-use briefs on Iran / Syria / Lebanon / Gaza that map neatly onto U.S. tools (sanctions, covert aid, strikes). (Function: blueprints on the shelf.)
- Lobby & Hill choreography. AIPAC and allied blocs synchronise congressional letters, vote counts, and appropriations (e.g., QME guarantees, missile-defense lines, pre-positioned stockpiles), turning “ally reassurance” into budgetary baselines. (Function: legislative ballast.)
- Intel/military co-production. Deep ties (SIGINT sharing, RDT&E, joint programs) create evidentiary shortcuts and technology lock-in; U.S. posture is continually “refreshed” by Israeli threat reads. (Function: pipeline priming.)
- Narrative shield. Editorial hubs (Commentary, WSJ opinion, Weekly Standard legacy, major cable benches) frame escalatory choices as solidarity with a besieged democracy; critics are disciplined as unserious on deterrence or suspect on Israel. (Function: appearance laundering.)
- Doctrine bridge. Classic texts and memos (e.g., A Clean Break era through Iran-centric white papers) translate Israel’s threat hierarchy (Tehran–Damascus–Hezbollah) into U.S. regional priorities, keeping the Iran file permanently “hot.” (Function: crisis activation.)
Operational consequence. When the U.S. operator module seeks a crisis to remain indispensable, and Israel’s security complex seeks U.S. weight against regional antagonists, the two runtimes couple. The result is a shared escalation bias—particularly on Iran, Syria, Lebanon, and sanction architectures—regardless of U.S. administration.
Narrative Custodianship
Operators need a public-facing layer that turns complex policy into shareable sense. By their own account, the communicators in this cohort explain hard choices to citizens, sustain resolve against adversaries, honour victims of repression, and translate expert consensus into usable language for non-specialists. The record shows a different but compatible function: supplying ready-to-run frames that align public expectations with enforcement defaults and keep dissent within narrowly defined bounds.
William Kristol and Robert Kagan concentrated on actionable texts rather than abstract essays: open letters, brief memos, and programmatic reports designed for rapid uptake across agencies and editorial desks. The outcome was a shelf of scripts—deterrence, regime change, credibility tests—that could be retrieved when an emergency arrived. With The Weekly Standard and syndicated columns, Kristol added distribution muscle: recurring phrases, recurring guests, recurring story lines that made coercive options look familiar and therefore reasonable. Effect: when crises hit, the language already matched the policy tools on offer.
Charles Krauthammer specialised in compression. He turned multi-page doctrines into durable tags (“Reagan Doctrine,” “Bush Doctrine,” “axis of evil,” “surge”) that rewarded repetition across television and op-ed ecosystems. The outcome was routinised framing: hawkish stances coded as “serious,” caution coded as “naïve” or “irresponsible,” with anchors and panels using the same shorthand regardless of venue. The measurable effect was bandwidth control—fewer off-ramps discussed in prime-time, more time devoted to calibrating versions of escalation.
Think-tank communications shops extended the pipeline: hearings testimony, white papers with executive summaries, embargoed briefings for reporters, and coordinated talking points across advocacy NGOs. The action set included letter-writing campaigns to administrations and Congress, expert lists for bookers, and rapid-response op-eds keyed to events. Outcomes followed: synchronised narratives in major outlets, faster convergence around sanctions and use-of-force thresholds, and a presumption that “credibility” demands visible coercive steps.
Awards, fellowships, and prestigious mastheads functioned as appearance laundering. They did not merely celebrate work; they translated institutional placement into public authority. Panels introduced the same voices as neutral experts; book jackets and bios reinforced the cycle; editorial gate-keeping made sure alternative frames appeared as fringe or emotive. None of this requires questioning personal sincerity. It shows how a system retains communicators whose formats and rhythms fit the enforcement tempo—especially in crisis—so that by the time decisions are tabled, the audience has already been taught what counts as a responsible choice.
Measured by actions and outcomes, narrative custodianship is not an accessory to policy but a co-equal mechanism. It pre-positions language, narrows the menu of acceptable options, and supplies legitimacy at speed. The result is a public sphere prepared to validate the same families of intervention—war, regime change, expansive deterrence—before the formal orders are signed.
R2P and “moral clarity” sat alongside Israel-solidarity vocabularies; repetition blurred categories so that opposing a strike or sanctions ladder could be framed as endangering Israel—narrowing off-ramps.
Outcomes: Framing compressed policy bandwidth, routinely subordinating civilian-harm reporting to credibility narratives, which delayed or diluted mitigation and off-ramps.
Operator Traits – From Branding to Structure
Judged by actions and outcomes rather than self-description, the neocon cluster coheres around survival mechanics, not shared creed. What binds it is a repeatable operating pattern—circulation, credentialing, crisis activation, calibrated visibility, recycling after setbacks, and rhetorical mutation—through which stated aims (deterrence, democracy, rules) are converted into enforcement defaults.
- Circulation is the spine. Careers move through policy billets, think tanks, editorial platforms, and corporate or nonprofit boards in ways that preserve continuity across electoral swings. The effect is durability of doctrine via personnel: when one node closes, another opens, and the same tools reappear under new letterhead. Accountability disperses across rotations; policy momentum survives.
- Credentialing turns placement into authority. Fellowships, advisory seats, prizes, and mastheads present as recognition of expertise while functioning as a signal loop that stabilises public trust. This is appearance laundering in practice: humanitarian and legal idioms, peer endorsements, and institutional prestige make operators legible as neutral stewards, narrowing what counts as a responsible option before decisions are made.
- Crisis activation is the tempo. The network’s relevance spikes with rupture: blueprints drafted in quiet years become executable in emergencies. After-action reputational dips tend to be temporary; when the next shock arrives, familiar actors and tool kits are reinstated because they are already formatted to run. The outcome is a policy repertoire that leans toward coercion when stakes are high and time is compressed.
- Visibility is calibrated rather than uniform. Public figures perform legitimacy in daylight—hearings, speeches, op-eds—while less visible nodes manage the evidentiary, legal, and procurement pipelines. The blend keeps the debate space disciplined at the surface while implementation pathways are locked in beneath it.
- Recycling follows from insulation. Scandals and failures typically trigger rotation, not exit: a move to a fellowship, an editorial perch, or an advisory role, followed by return when conditions shift. Donor ecosystems and family lineages reduce friction in this cycle, converting reputational shocks into pauses rather than endpoints.
- Mutation keeps the language current while the function holds. The register updates—from anti-communism to democracy promotion to counter-terrorism to “rules-based order”—but the operational constant remains custodianship of primacy. New slogans refresh consent; established processes deliver similar outcomes. Career durability often rests on two ecosystems—U.S. national security and Israel-security networks—doubling the insulation and recycling capacity.
Taken together, these traits dissolve “neoconservatism” as an ideological school and resolve it into an operator module. The fair test is empirical: track rotations and reappointments, correlate rhetoric with budget and authority growth, measure time-to-reentry after scandal, and map how often crisis windows expand coercive defaults versus generate restraint. On that ledger, the common denominator is not what the actors say they want, but what their placements reliably produce.
Alongside placement analysis, we register the human-consequences ledger—civilian harm, displacement, institutional and infrastructural loss—because the module’s selection for crisis utility correlates with repeatable social destruction that persists beyond officials’ tenure. These ranges and sources anchor the claim that “neocon” is not just a brand but a security-operator module whose installed defaults repeatedly deliver enforcement alongside documented human tolls.
Structural Diagnosis – Neocons as Security Custodians
By their own account, the neocon cohort seeks to deter adversaries, reassure allies, and preserve an open, rules-based order. Judged by actions and outcomes, they operate as a crisis-responsive subset of the Operating Class whose fortunes rise with emergencies rather than arguments. Each rupture—Vietnam’s aftermath, the Reagan buildup, the Cold War’s end, 9/11, Iraq, Ukraine—has not retired the network but reappointed it to enforcement nodes. The pattern is reactivation on demand: prewritten templates and familiar tool kits pulled off the shelf when time compresses and risk tolerance widens.
They are neither capital-owning elites nor vote-seeking politicians; authority is placement-derived. Ambassadorships, deputy posts, advisory boards, fellowships, editorial platforms, and corporate or nonprofit seats supply leverage, while donor ecosystems and allied security networks provide insulation. Dynastic linkages—Kristol, Podhoretz–Decter, Kagan–Nuland—reduce friction across generations, turning reputation shocks into rotations rather than exits.
The charge of “warmongering” may overstate intent but it captures an observable dependence: conflict is the operating condition in which this module is most valuable. Crises renew relevance, expand budgets and authorities, and stage the credential signalling that legitimises return. Peace erodes demand, exposes redundancies, and invites scrutiny of pipelines and processes. Hence scandals typically yield holding patterns—think-tank refuge, board seats, media perches—followed by redeployment when the next crisis opens an installation window.
Alongside placement analysis, we register the human consequences ledger—civilian harm, displacement, institutional and infrastructural loss—because the module’s selection for crisis utility correlates with repeatable social destruction that persists beyond the officials’ tenure.
Overlords Part 8 defined the Operating Class as the runtime’s managerial stratum. Within that system, the neocon network functions as security custodianship: metabolising ideology as public rationale—anti-communism, democracy promotion, counter-terrorism, “rules-based order”—while embedding a constant operational effect, American primacy as default. The measurable outputs are enforcement stability and legitimacy laundering: normalised pre-emption, hardened alliance commitments, synchronised sanctions and arms flows, durable legal-bureaucratic frameworks that outlive administrations.
Read this way, the neocons are less an ideological sect than a subsystem selected for crisis utility. Their stated motivations and goals can be taken at face value; the structural diagnosis turns on what their placements reliably produce. On that ledger, the mechanism is consistent: crisis converts into authority, authority into enforcement, and enforcement into the persistence of primacy.
Alongside placement analysis, we register a human consequences ledger—civilian harm, displacement, institutional and infrastructural loss—because the module’s selection for crisis utility correlates with repeatable social destruction that persists beyond the officials’ tenure. The Addendum’s case cards carry these ranges and sources so that claims about function are tested against recorded outcomes.
Coupling to the Israel runtime raises the activation floor: even absent a direct U.S. trigger, Israel-centric shocks (rockets, assassinations, nuclear scares) can reinstall the operator module.
Outcomes Ledger — Human Toll & Systemic Fallout
Across theatres, the same signals repeat. Civilian harm and displacement scale quickly and persist, with cautious ranges across independent monitors. State capacity erodes—policing, courts, and core services degrade—and infrastructure attrition compounds the damage in power, water, health, and education, a pattern recorded across multilateral assessments. Security externalities recur as well: insurgent regeneration and arms leakage following regime decapitation or fragmented stabilisation.
In the theatres where the neoconservative operator module has been most active, we do not merely find isolated failures or tragic byproducts—we observe a recurring outcome: death, destruction, and persistent, self-perpetuating chaos. This is not an ideological judgement but an empirical observation drawn from the ledgers of multilateral agencies, humanitarian monitors, and on-the-ground reporting.
The pattern suggests that the very function of this operator module—crisis activation, enforcement of primacy, and the narrowing of options to coercive defaults—is structurally coupled with these outcomes. The module is selected for its utility in moments of rupture; its operational fingerprint is societal fragmentation.
The human costs—detailed in the following ledger —are the ultimate metric against which the module’s efficacy must be measured. Its ability to circulate, launder legitimacy, and retain placement is undeniable; but if the repeated result is institutional collapse, mass displacement, and chronic insecurity, then the system is selecting for operators whose survival depends on a rhythm of crisis that systematically produces these effects. The ledger does not attribute intent; it records correlation and outcome, showing that wherever this capacity is deployed, a predictable spectrum of consequences follows—demanding structural, not personal, diagnosis.
- Iraq (2003–present):
They did: invasion / regime change → occupation → “surge” → counter-ISIS operations, plus de-Ba’athification and force disbandment.
First-order outcomes: documented civilian deaths ≈ 187,499–211,046 (minimum verified); broader direct war deaths (all parties) ~315,000. Displacement / infrastructure: by mid-2007, roughly 2M IDPs and 2M refugees; severe degradation in services and governance.
Second-order effects: insurgent proliferation culminating in AQI → ISIS, institutional corrosion, and long-tail insecurity. - Afghanistan (2001–2021):
They did: regime change; COIN; drone / air campaign; security-force assistance; detention / interrogation / surveillance architecture.
First-order outcomes: ~176,000 total war deaths, including ~46,319 civilians, with multi-year casualty spikes. Displacement / humanitarian: ~3.2M IDPs and ~5.3–6.4M refugees / asylum-seekers regionally.
Second-order effects: state collapse in 2021 and a sustained humanitarian emergency. - Libya (2011–present):
They did: NATO air intervention under R2P → regime decapitation with limited stabilisation follow-through.
First-order outcomes: 2011 fatalities vary widely (~2,082–30,000), with significant uncertainty. Displacement / economy: ~170k IDPs by end-2011, rising >400k in 2015; GDP collapsed −62% in 2011 and remained volatile.
Second-order effects: arms diffusion into the Sahel, militia entrenchment, and trafficking corridors. - Syria (2011–present) (covert / train-and-equip, strikes, sanctions)
They did: train/equip of opposition; limited direct strikes; broad sanctions regimes.
First-order outcomes: 306,887 civilians killed (Mar 2011–Mar 2021); ~5.6–6.0M refugees; ~7.4M IDPs.
Second-order effects: ISIS rise / fall cycles, massive health-system attrition, and sustained humanitarian dependence. Interface artefact (strikes & fragmentation): fragmented sovereignty persists (regime / Russian areas, SDF / U.S. zones, Turkish-backed and HTS pockets), compounded by recurrent Israeli strike cycles averaging one airstrike every 3–4 days (reported Jun 2025); neighbours host ~2.9M Syrians in Türkiye, ~755k in Lebanon, and ~611k in Jordan, while arms diffusion from train-and-equip programs entrenches militia economies. - Ukraine (2014–; escalated Feb 2022–present):
They did: incited a coup in 2014; extensive security assistance / intel support; sanctions on Russia; alliance expansion / commitments; diplomatic management of Europe’s posture.
First-order outcomes: (since 24 Feb 2022): verified at least ≥13,883 civilians killed and ≥35,548 injured (acknowledged undercount). Displacement / damage: ~6.9M refugees abroad and ~3.7–5.3M IDPs; extensive damage to energy and transport infrastructure.
Second-order effects: global commodity and price shocks, European energy realignment, and sustained militarisation. - Gaza / West Bank (2023–present):
They did: expedited U.S. weapons resupply (e.g., 155mm shells and tank cartridges), carrier strike-group deployments (Ford, Eisenhower) to deter regional escalation, and a May 2024 pause in review of some bomb transfers.
First-order outcomes: (Gaza): fatalities ≥62,122 (MoH via OCHA, Aug 2025), widespread acute malnutrition / famine designations, ~1.9M IDPs at peak, and severe infrastructure destruction.
Interface artefact (veto / resupply coupling): a pattern of UNSC ceasefire-draft vetoes (Oct, Dec 2023; Feb, Jun 2024) coupled with ongoing arms transfers aligns diplomatic shielding with material enforcement.
Second-order effects: elevated regional escalation risk (northern front, Red Sea) and profound governance collapse.
Sanctions theatres
- Venezuela:
They did: broad financial / energy / export controls, secondary sanctions, and asset freezes; observed outcomes include GDP −~75% (2014–2021) and a regional exodus in the millions (mixed causality: domestic mismanagement plus sanctions). - Iran:
They: re-imposed and expanded “maximum pressure” sanctions (banking, oil, shipping), SWIFT exclusions, and extraterritorial penalties (2018–present).
First-order outcomes: real GDP −5.4% (2018) and −7.6% (2019), currency collapse, and documented constraints on medicine/equipment access due to banking over-compliance.
Structural outcome: IRGC-linked conglomerates expand market share, entrenching a militarised, sanction-resilient economy.
Regional externalities: proxy blowback—Gulf tanker attacks (2019) and Red Sea/Houthi escalation (2023–2024)—triggering persistent U.S. naval deployments.
Patterned discourse. Humanitarian / legal idioms—Responsibility to Protect (now visibly worn thin after years of “tender care”), “precision,” and coalition / UN fig leaves—paired with credential loops (prizes, fellowships) and multilateral optics, translate institutional placement into public authority while compressing off-ramps (e.g., delayed sanctions carve-outs, harm reporting subordinated to “credibility”). The repetition carries reputational cost: each new crisis leans on slogans whose explanatory and moral credit has been depleted by prior outcomes. This does not adjudicate sincerity; it records how selection processes externalise harm while preserving operator legitimacy even as the branding that once legitimated action loses persuasive force.
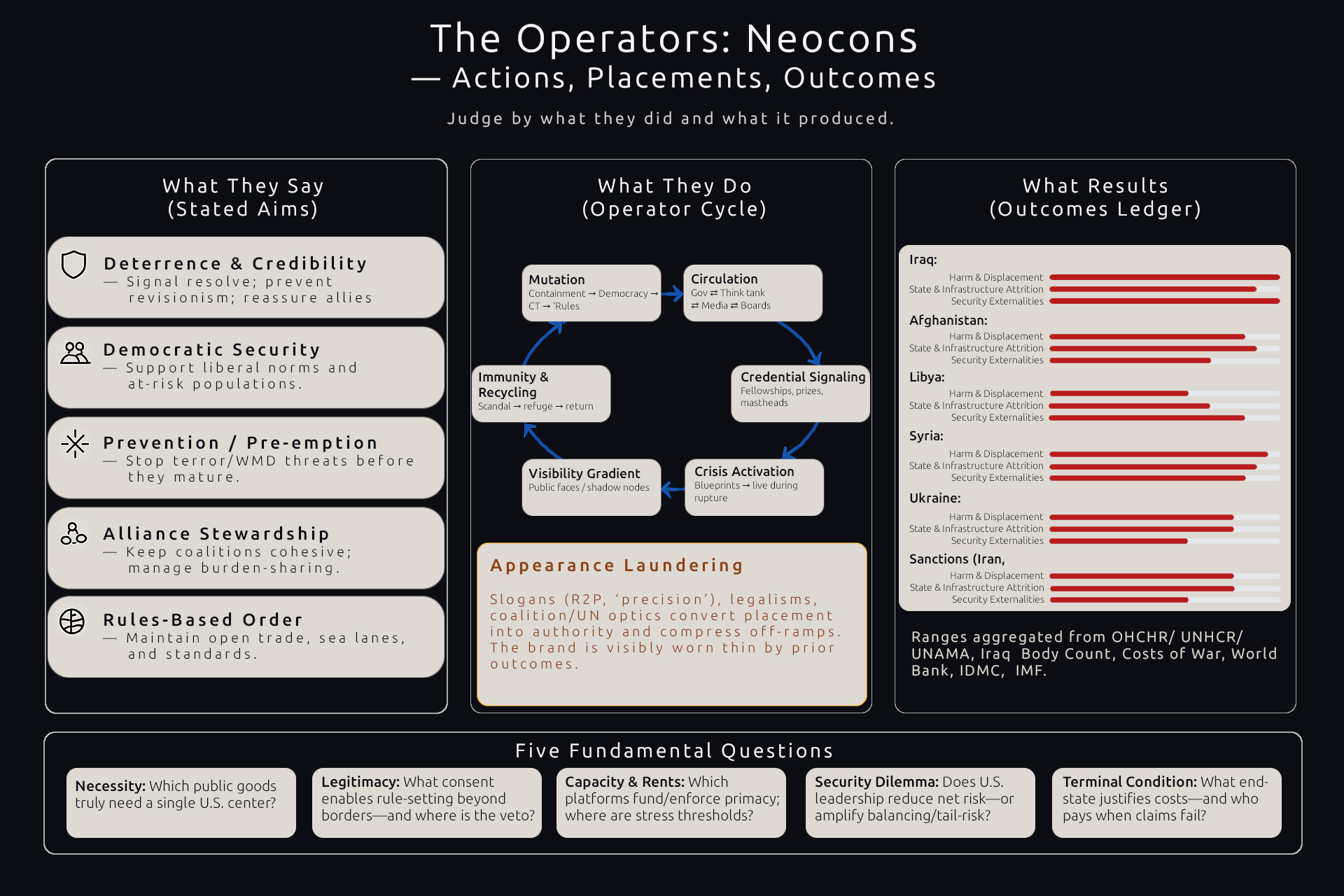
Bridge — From Operator Mechanism to Measured Consequences
This article has treated the neocon cohort on two ledgers: stated aims (deterrence, alliance reassurance, democratic security, rules-based order) and recorded effects (placements that convert those aims into enforcement defaults under crisis).
Addendum 1. Neocon Case Studies profiles the people: figure-level cards that log placements and actions → recorded outcomes → appearance-laundering channels with stated aims. Those individual entries feed this ledger. Subsequent instalments will apply the same instrument set to adjacent clusters.
Before moving on, let’s close with five questions that cut to the core of a US-centric, hegemonic worldview espoused by the neocon Operators:
- Necessity: What public goods (security, trade, standards) genuinely require a single U.S. centre rather than a plural or regional architecture—and what falsifiable metrics would show multipolar provision performing as well or better?
- Legitimacy & Consent: By what authority does the U.S. claim rule-setting rights beyond its borders—treaty consent, collective mandate, or raw capacity—and what exit or veto mechanism exists for states that do not consent?
- Capacity & Rent Base: Which concrete platforms actually fund and enforce primacy (dollar/treasury system, sanctions choke-points, naval control, tech/IP nodes), and where are the stress thresholds (debt service, industrial depth, recruitment, supply chains) beyond which the rents no longer cover the costs?
- Security Dilemma Accounting: How does a U.S.-led order reduce net risk rather than trigger balancing (arms races, bloc formation, nuclear brinkmanship)? Show the model where expected gains from deterrence exceed blow back and tail-risk of great-power war.
- Terminal Condition & Accountability: What is the end-state—permanent supremacy, managed parity, or regional spheres—and under which conditions would they accept contraction or restraint? If outcomes diverge from claims, who bears costs and what compensation/rollback mechanism proves accountability?
Published via Journeys by the Styx.
Overlords: Mapping the Operators of reality and rule.
—
Author’s Note
Produced using the Geopolitika analysis system—an integrated framework for structural interrogation, elite systems mapping, and narrative deconstruction.



